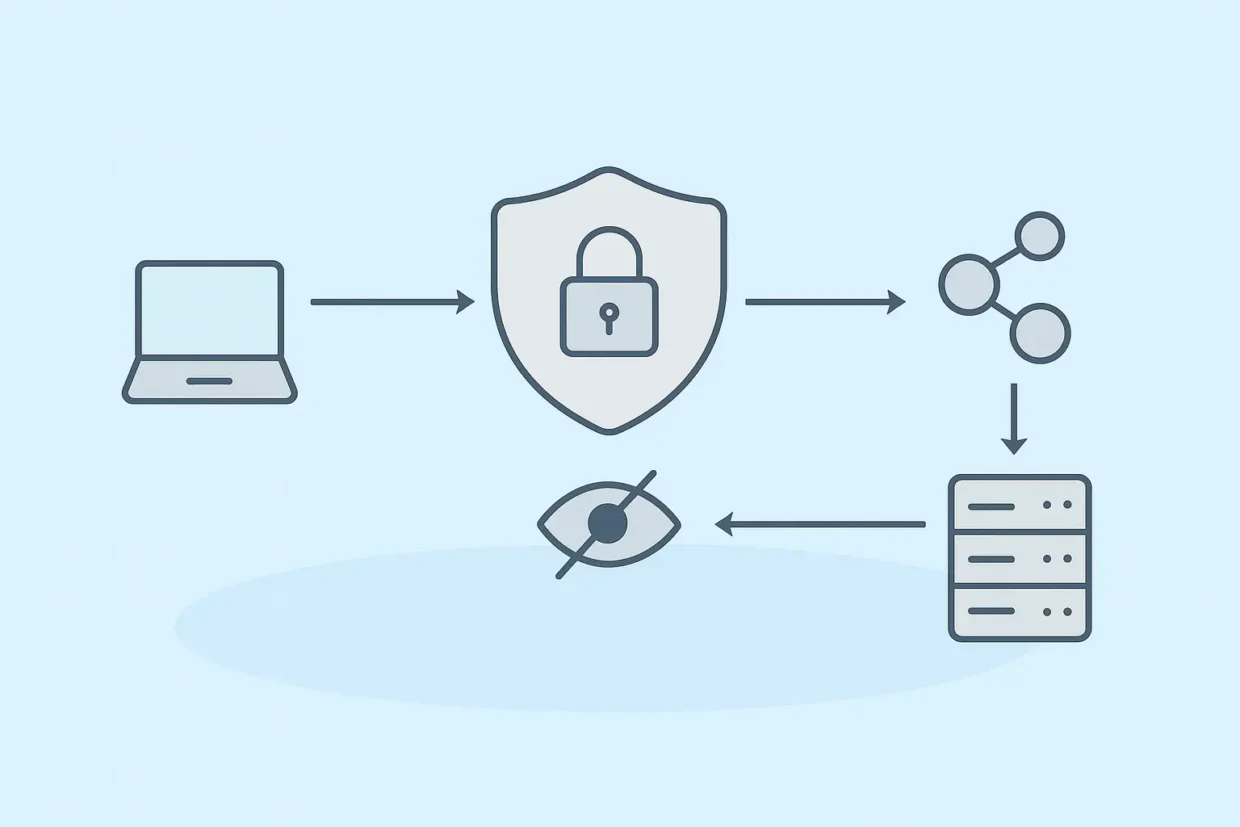
The first time I came across the term TLS proxy, I had to admit—it totally went over my head. Sure, I knew a thing or two about encryption and security, but what does a proxy server have to do with my everyday browsing? After a few hours of Googling and a couple of coffees later, it all started to make sense—TLS proxy is basically a nosy gatekeeper standing between me and what I do online. And it’s absolutely worth paying attention to.
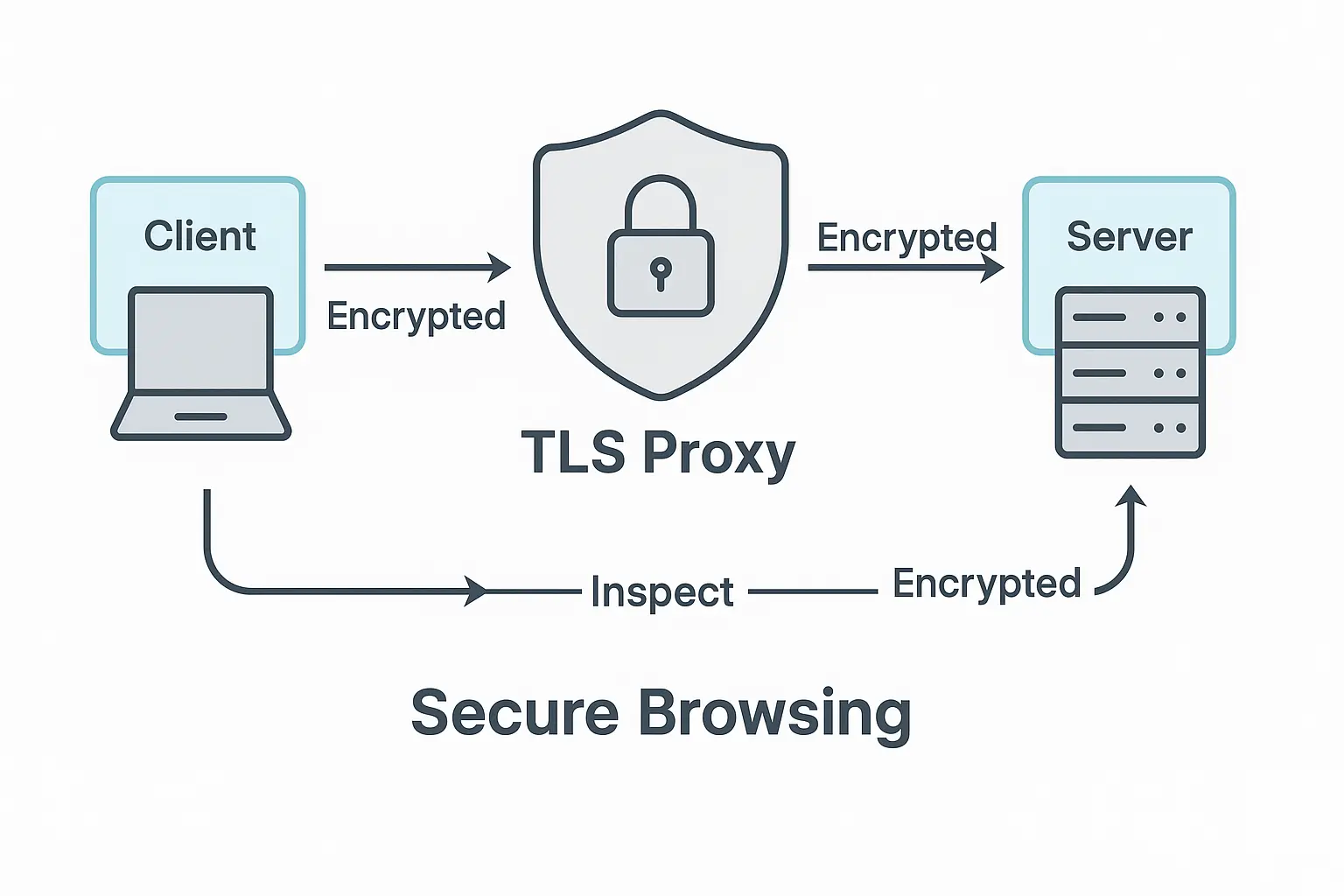
TLS proxy (short for Transport Layer Security proxy) is a middleman between my device—say, my laptop—and a web server. More precisely, it’s a smart “box” (not necessarily physical) that can decrypt encrypted traffic, peek at it, and then re-encrypt it before sending it off. Sounds kind of scary at first, but it actually makes a lot of sense—especially from a security perspective.
Why Would Anyone Want to Decrypt Encrypted Traffic?
Have you ever wondered why someone would want to “peek” into encrypted communication? I used to think HTTPS and TLS were untouchable. But here’s the catch: when everything is encrypted, how can a company protect its employees from phishing or malware if it can’t see what’s being downloaded?
TLS proxy solves this by ending the encryption between me and the proxy, checking the content, and then creating a new encrypted connection to the target server. From the outside, everything remains protected, but inside, it can be scanned, filtered, or inspected.
Termination vs. Pass-through – The Two Faces of TLS Proxy
In practice, there are two types of TLS proxy – and they behave quite differently.
- TLS termination proxy: It actually terminates the encrypted connection from the client, decrypts everything, inspects it, and then re-encrypts and forwards it. This is widely used in companies, schools, or data centers where insight into traffic is essential.
- TLS pass-through proxy: On the other hand, it just “passes” encrypted traffic without decrypting anything. Like mailing a sealed envelope – the proxy just delivers it without opening. It’s great for privacy but doesn’t allow for any inspection.
TLS Proxy: Pros and Cons
Pros:
- Enables control over encrypted traffic – ideal for IT security teams.
- Centralized certificate and policy management.
- Helps with compatibility for older systems that struggle with newer TLS versions.
Cons:
- The proxy sees decrypted data – you have to trust it.
- Poor configuration can lead to more problems than benefits.
- Added latency and processing load – decrypting isn’t free.
How TLS Proxy Works “Under the Hood”
The process starts when a client initiates a connection with the proxy. In termination mode, the TLS handshake takes place between the client and the proxy. The proxy decrypts the data, performs inspection or security checks, and then establishes a new encrypted connection with the target server.
In tunneling mode, it’s simpler – the proxy creates a tunnel and just forwards the data. It doesn’t see anything, but also can’t protect anything.
What Does a TLS Proxy Do to Network Performance?
Now we’re getting into something that always makes me a bit nervous—performance. Any tool that “touches” traffic can slow the network down. And TLS proxy is no exception. If it’s doing TLS termination, it has to decrypt the data, analyze it, and then encrypt it again. Not a light task—especially when you imagine hundreds or thousands of simultaneous connections.
Increased latency? Yep.
When everything passes through a proxy, there’s always some delay—what we call latency. Sometimes it’s just a few milliseconds, other times you really feel it. That’s why things like hardware acceleration or session resumption are so often used.
Load? Definitely.
A proxy that decrypts and re-encrypts traffic has to be packed with serious processing power—either a strong CPU or dedicated encryption chips.
Technical Challenges TLS Proxy Has to Face
No tool is perfect, and that’s definitely true for TLS proxy. Several things can make the whole setup a real headache:
- Trusted certificate required – If the client doesn’t trust the proxy’s certificate, the connection won’t go through.
- TLS version support – Every server may run a different version of TLS or use different algorithms—the proxy needs to adapt to all of them.
- Security risks – The proxy has access to decrypted data. If someone compromises the proxy, it’s a major problem.
- Performance – It’s a resource hog, especially under heavy traffic.
- Configuration complexity – One small mistake and the whole thing breaks—or worse, creates security holes.
Is TLS Proxy the Same as a VPN?
This is a common question, and the answer is: absolutely not.
- VPN secures the entire device connection. Everything you do online—every click, every connection—goes through an encrypted tunnel.
- TLS proxy only handles specific traffic—usually from a browser or app—and it may inspect that traffic too. VPN, on the other hand, tries not to look at anything—it just protects.
In terms of privacy and anonymity, VPN wins. TLS proxy is more of a corporate tool for filtering and inspecting encrypted traffic.
Can TLS Proxy Replace a VPN?
Short answer? Nope.
VPN protects everything—your entire device, every app. It also hides your IP address, secures you on public Wi-Fi, and ensures privacy.
TLS proxy can protect against threats and monitor web activity, but:
- It doesn’t encrypt everything.
- It’s not anonymous.
- You have to trust it.
In short: both technologies have their place, but they’re not interchangeable.
Final Thoughts
TLS proxy is a powerful—yet slightly controversial—tool. It helps organizations inspect and secure encrypted traffic. But it comes with challenges—performance overhead, trust issues, and complex setup.
If you’re into network security, it’s definitely worth understanding how TLS proxy works. But if privacy and anonymity are your top goals, a VPN is the way to go.
Frequently Asked Questions (FAQ)
Is TLS proxy safe?
Yes, if configured correctly and you trust the certificate authority. But it does see decrypted data.
How do I know if my company uses TLS proxy?
Sometimes your browser will display a certificate warning or show a different issuer in the HTTPS connection. That’s a clue.
Can I use TLS proxy at home?
Technically yes, but most people don’t need it. It’s mainly used in enterprise environments.
Does TLS proxy slow down the internet?
It can. Especially if it’s not scaled properly or lacks hardware acceleration.
What’s the difference between a TLS proxy and HTTPS proxy?
HTTPS proxy works on the protocol level but may not inspect encryption. TLS proxy focuses specifically on encryption and inspection.
Can TLS proxy stop malware?
Yes. Since it sees encrypted traffic, it can detect hidden threats within HTTPS.