You’ve seen that little “Secure Core” switch inside your Proton VPN app. Maybe you even flipped it on thinking, this has to be the ultimate protection – it’s literally called Secure Core. It sounds like activating some kind of digital force field – more routing layers, tighter control, maybe even total invisibility. It feels like a power move… at least until you find out what it really does.
But what if I told you that for 99% of your online life—your streaming, your gaming, your casual browsing—clicking that button is not only pointless, but it’s actively making your experience worse?
Secure Core is one of the most powerful features in the entire VPN industry. It’s also one of the most misunderstood. It’s not a “go faster” button. It’s not a “make me 100% invisible” button.
It’s a highly specialized tool for an extremely specific, and frankly, terrifying, type of threat. It’s the digital equivalent of an armored tank. And you don’t take a tank to the grocery store.
So, let’s get real. Let’s pull back the marketing hype and talk about the brutal truth of what Secure Core is, what it’s reallybuilt to defeat, and—most importantly—when you should absolutely, positively turn it off.
What Is Proton Secure Core? (Hint: It’s Not Just a “Double VPN”)
You’ve heard of “multi-hop” or “double VPN.” That’s when your traffic goes from your computer, to one VPN server, then to another VPN server, before finally going to the website you want. Secure Core is that, but on steroids.
The difference is in where that first hop goes.
Proton doesn’t just send you to any random server. With Secure Core enabled, your traffic is always routed first through one of three countries: Switzerland, Iceland, or Sweden.
Why those three? Because they have some of the most legendarily strong privacy laws on the planet. They are legal fortresses, far removed from broad surveillance agreements.
But this is where it gets into James Bond territory. Proton didn’t just rent servers in these countries.
They own and operate every single piece of Secure Core hardware. They didn’t just stick them in a normal data center rack and installed them in high-security, absurdly-protected locations:
- Sweden: The servers are located in an underground data center.
- Iceland: The infrastructure sits on a secure former military base.
- Switzerland: The servers are in a high-security facility requiring biometric access.
On top of that, all these servers are protected by full-disk encryption. Even if an armed squad breached the military base, fought their way underground, and physically stole the server, the data on it would be useless, unreadable garbage.
This is not paranoia. This is a very specific, very expensive defense against a very specific, very powerful enemy.
The Real Enemy: The “Correlation Attack”
So, why build this digital fortress? Secure Core is designed to defeat one of the most sophisticated attacks a VPN user can face: the Correlation Attack (also called a timing attack).
Here’s how it works in simple terms:
Imagine a powerful state-level agency wants to spy on you. A normal, single-hop VPN is a problem for them, but not an impossible one. To break it, they just need to be in two places at once:
- They watch your internet connection. They tap your local ISP and see that you are sending encrypted data packets to a VPN server in New York.
- Watch the exit server. At the exact same time, they are monitoring the network at the New York data center. They see those same-sized data packets leaving the server and heading to, say, a whistleblower’s website.
They can’t read the data, but they don’t need to. By matching the timing and size of the packets going in with the packets coming out, they can “correlate” the traffic. They have just proven, with high certainty, that you are the one visiting that sensitive site. Your anonymity is gone.
This is what Secure Core is built to kill.
When you turn it on, the attacker’s job becomes practically impossible.
The spy watching your ISP? They only see you sending data to that military base in Iceland. The spy watching the exit server in New York? They only see data coming in… from Iceland.
To make the connection, the attacker would have to simultaneously monitor your home ISP and compromise Proton’s physically-owned, biometric-locked, full-disk-encrypted server on a military base in a privacy-haven country.
The chain is broken. The scent is lost.
The Other Enemy: The Censor’s Great Firewall
There’s a second threat this helps with: Deep Packet Inspection (DPI). This is the technology used by regimes in China, Russia, Iran, and others to not just block websites, but to detect and block VPN traffic itself.
They use sophisticated “traffic fingerprinting” to analyze your data. Even though it’s encrypted, it has a certain “shape” that screams “I AM A VPN!” When they spot it, they can throttle or kill your connection.
Secure Core doesn’t actively obfuscate traffic like specialized Stealth or Obfuscated servers do, but it makes fingerprinting much harder by mixing user traffic inside its protected core network.
By the time it leaves that core server, it looks less like a single user trying to bypass censorship and more like legitimate, aggregated traffic from a neutral data center. It’s much harder to fingerprint.
So, Who Really Needs This? The 1% Club
If you’ve read this far, the answer should be pretty clear. You need Secure Core if your “threat model” isn’t a hacker in a coffee shop, but a nation-state with billions of dollars and surveillance-level resources.
Secure Core is available only on ProtonVPN Plus and Unlimited plans, not in the free version.
This is the 1% user list:
- Investigative Journalists: Especially those communicating with sensitive sources or operating in repressive regimes.
- Activists & Whistleblowers: People whose work directly challenges authoritarian governments and who face active surveillance.
- Diplomats & High-Level Executives: Anyone whose communications (political or corporate) would be a high-value target for foreign intelligence.
- Anyone in a High-Risk Jurisdiction: If you live in a country known for actively monitoring, blocking, and punishing VPN use, Secure Core gives you that critical extra layer of defense.
This is the kind of technology that human rights organizations broadly recommend for people in these high-stakes situations—tools that can help circumvent censorship and protect anonymity when lives are on the line.
If you are not on this list… you probably don’t need it.
The Brutal Truth: When You Must Turn Secure Core OFF
Here it is: for 99% of us, Secure Core is massive overkill. It’s an armored tank for a trip to the mall, and it comes with one, massive, unavoidable trade-off: It will noticeably slow down your internet speed.
Every hop you add, every extra layer of encryption, adds latency and kills bandwidth. A regular Proton VPN connection is already incredibly fast, often losing only 15-16% of the base speed, which you’ll barely notice.
But Proton Secure Core? That’s a different story.
Independent tests in 2024/2025 found that using Secure Core was, on average, an additional 35% slower than a regular Proton VPN connection. That’s a huge hit on top of the already minimal speed loss.
The real-world impact is even starker. I saw one user’s speed test on a 100 Mbps connection that tells the whole story:
- Standard Server (US): 98.72 Mbps
- Secure Core (via Swiss to US): 58,24 Mbps
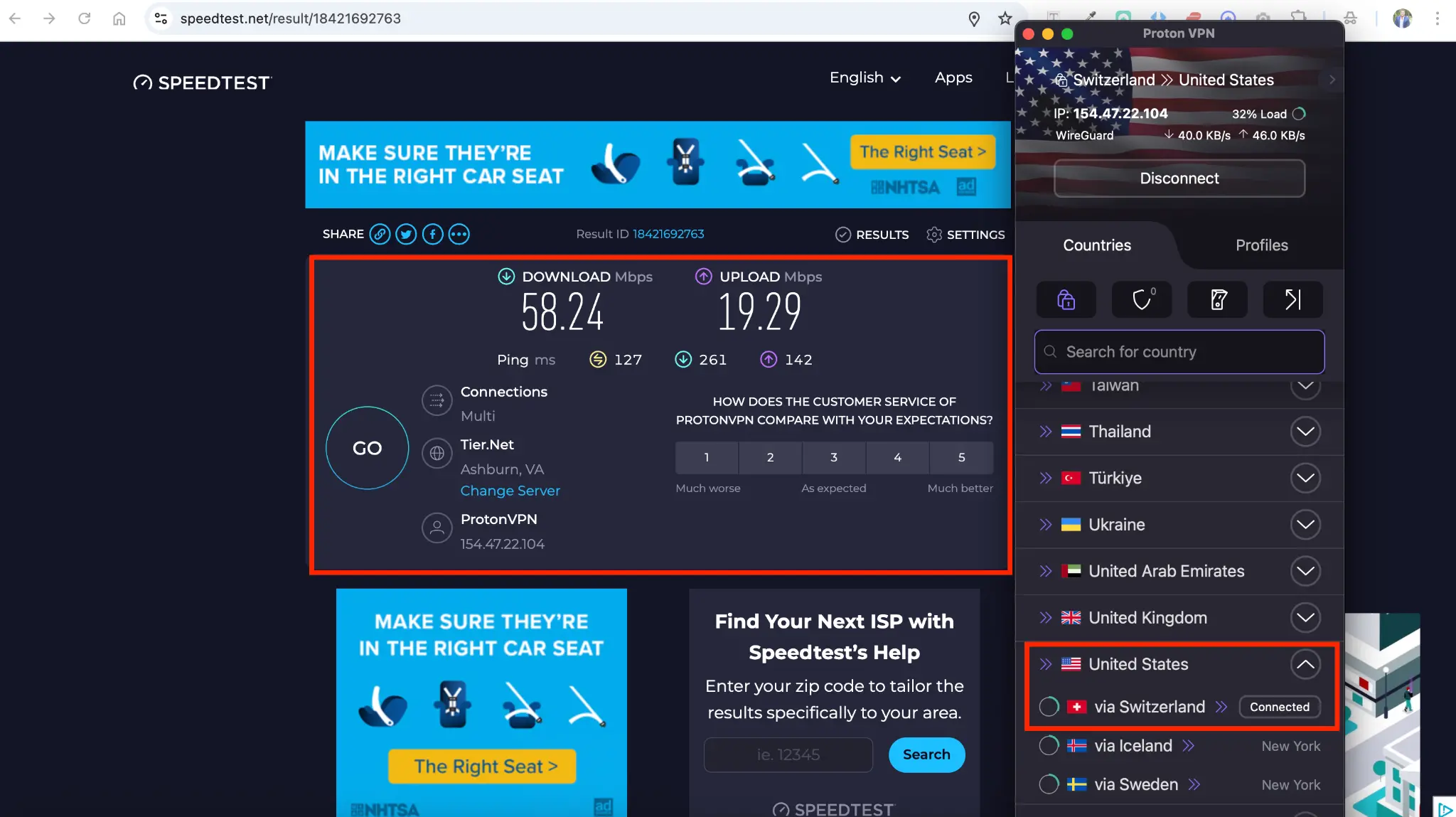
That’s an 40% drop in performance.
And that’s just download speed. The killer for gaming and video calls is latency (ping). A good ping is under 50ms. Secure Core connections can easily add 100-200ms of lag, making any real-time activity an impossible, stuttering nightmare.
| Your Activity | Standard Proton Server (The Right Choice) | Secure Core (The Wrong Choice) |
| Streaming (Netflix, etc.) | YES. Blazing fast. You’ll get 4K streaming with no buffering. | NO. You’re adding massive latency and killing your bandwidth. Get ready for the buffering wheel. |
| Online Gaming | YES. Low latency gives you a competitive, lag-free experience. | ABSOLUTELY NOT. The 100ms+ ping will get you kicked from the server. It’s unplayable. |
| Torrenting / P2P | YES. Use a P2P-optimized server for the fastest possible download speeds. | NO. Why would you cut your download speed by 40%? It’s just slow and unnecessary. |
| Daily Browsing | YES. Protects you from ISP tracking and public Wi-Fi hackers with minimal speed loss. | NO. It’s overkill. You don’t need an underground bunker to check your email. |
The Final Verdict: It’s a Tool, Not a Default Setting
So, what’s the truth about Secure Core?
It’s one of the most robust, physically-secure, and technically brilliant privacy features ever offered to the public. It is a serious tool for serious threats.
It is not a “better VPN” button.
For the vast majority of us, our “threat model” is just our ISP selling our browsing data, or a hacker trying to snoop on us at a Starbucks. For that, a standard Proton VPN server is the perfect, high-speed solution.
Think of it this way: Proton has built you a garage. In it, you have a lightning-fast sports car (the standard server) and an armored tank (Secure Core).
Ninety-nine percent of the time, you should take the sports car. But it’s an incredible feeling to know that if the world goes sideways, you’ve got that tank sitting there, ready to go.
So, be smart. Understand your real risks. And please, for the love of all things fast, stop using the tank to go get groceries.
FAQ: ProtonVPN Secure Core
Does Secure Core make ProtonVPN more secure?
Yes, but only against highly advanced attacks like correlation or timing attacks. For everyday use, a regular ProtonVPN server already offers strong encryption and full protection.
Why does Secure Core slow down the connection?
Because your traffic travels through two VPN servers instead of one, often across continents. The extra routing increases latency and reduces download speed by 30–40%.
Which countries host Secure Core servers?
Switzerland, Iceland, and Sweden – all known for strong privacy laws and independent data protection regulations.
Is Secure Core included in the free plan?
No. Secure Core is available only on ProtonVPN Plus and Unlimited plans. Free users can still enjoy full encryption, but without this advanced multi-hop routing layer.